Cybersecurity: Asset Inventory & How to Protect It, according to a Product Security Manager
 Construction companies harbor a lot of data—architectural drawings, bid documents, contracts, and other financial agreements. The process of a construction project is also often a disjointed one. That is to say, working alongside subcontractors, architectural firms, third-party prefab shops and 3D printers, and so forth, offers the advantage of speed to a single construction company, but it also inherently introduces extra complexity.
Construction companies harbor a lot of data—architectural drawings, bid documents, contracts, and other financial agreements. The process of a construction project is also often a disjointed one. That is to say, working alongside subcontractors, architectural firms, third-party prefab shops and 3D printers, and so forth, offers the advantage of speed to a single construction company, but it also inherently introduces extra complexity.
Construction being data-rich and complicated, it’s therefore no surprise that companies in the construction sector are becoming an increasing target for cybercrooks. In 2021, Construction Dive reported that construction was the #1 industry hit by ransomware (ahead of finance, astoundingly), according to a comprehensive, multinational report by Nordlocker. Similarly, in a report by the Associated General Contractors of America (AGC), concerns like data breaches, cyber extortion and ransomware, fraudulent wire transfers, breach of intellectual property, and breaches of bid data were all considered high cybersecurity risks for construction businesses.
Cybersecurity in construction is a mission-critical driver for keeping your company agile to respond to growing cyberthreats. And as every phase of the construction process creates a possible attack vector that would-be cybercriminals may look to exploit, it’s therefore crucial that companies increase cyber awareness and best practices among their employees, and implement antifragile business structures that help empower a strong first line of defense in your workers.
A cybersecurity vector you’ll want to shore up: Your asset inventory, which we’ll turn our attention to in this article.
Jump Ahead:
- Why Is Asset Inventory Important in Cybersecurity?
- Integration Partners and Building Security Best Practices as a Backbone to Interoperability
- Shore Up Multi-User Accounts and Ensure Proper Permissioning
- Ensure (and Educate Employees) Proper Settings Are Configured for Item-Level Tracking
- Hire Cybersecurity Talent (and What to Look for)
Why Is Asset Inventory Important in Cybersecurity?
On the surface, your tool and equipment inventory may not strike you as valuable to cybercriminals—full of service records, perhaps individualized short-hands used by your tool team to streamline processes, and other item-level information one might consider pedestrian.
In reality, tool theft is a rising concern costing the U.S. an annual $300 million to $1 billion. What’s more, as the physical and digital realms continually blur, access to, for example, equipment location records become more valuable to tech savvy criminals looking to track down possible paydays.
 I recently had the opportunity to sit down with Zach Costello, a Senior Product Security Manager at Milwaukee Tool, to discuss cybersecurity as it relates to asset inventory management, and how inventory managers and tool crib managers can manage their ONE-KEY™ inventories in a more secure manner.
I recently had the opportunity to sit down with Zach Costello, a Senior Product Security Manager at Milwaukee Tool, to discuss cybersecurity as it relates to asset inventory management, and how inventory managers and tool crib managers can manage their ONE-KEY™ inventories in a more secure manner.
Costello started his career in information technology (IT) routing, switching, and IP telephony (aka: voice over IP). He eventually transitioned to a security engineering role supporting a data loss prevention tool. Thriving in this role, he eventually became a security manager, later shifting his focus from organizational security (aka: IT security) to product security (i.e., safeguarding the security of a product a company offers, how the customer perceives that security, as well as how the customer can implement the solution in a secure way).
Today, Costello is broadly responsible for security and compliance of our One-Key application, connected products, and ensuring from an application security perspective the app is developed and deployed in a secure way to protect end users as well as Milwaukee Tool. He manages a team of security analysts, engineers, and architects that work to keep the application infrastructure secure from design to deployment. They also collaborate with security teams across Milwaukee Tool’s corporate ecosystem to keep the company and our customers’ data secure.
Bringing this specialized subject matter expertise, I looked to Costello as an advisor to offer cybersecurity principles most relevant to inventory managers and business owners in keeping their inventory data secure.
Here’s some of his advice:
Integration Partners and Building Security Best Practices as a Backbone to Interoperability
As the industry looks to execute projects with a continually narrowing talent pool, interoperability and data governance are of growing concern. That said, companies staring down the barrel of increasingly complicated building projects often look to building partners (e.g., subcontractors) and technology partners (e.g., software integrators) to facilitate these projects’ completion. Experts agree that software integration in the industry is going to increase by necessity (and with it the need for data security best practices grow increasingly critical). 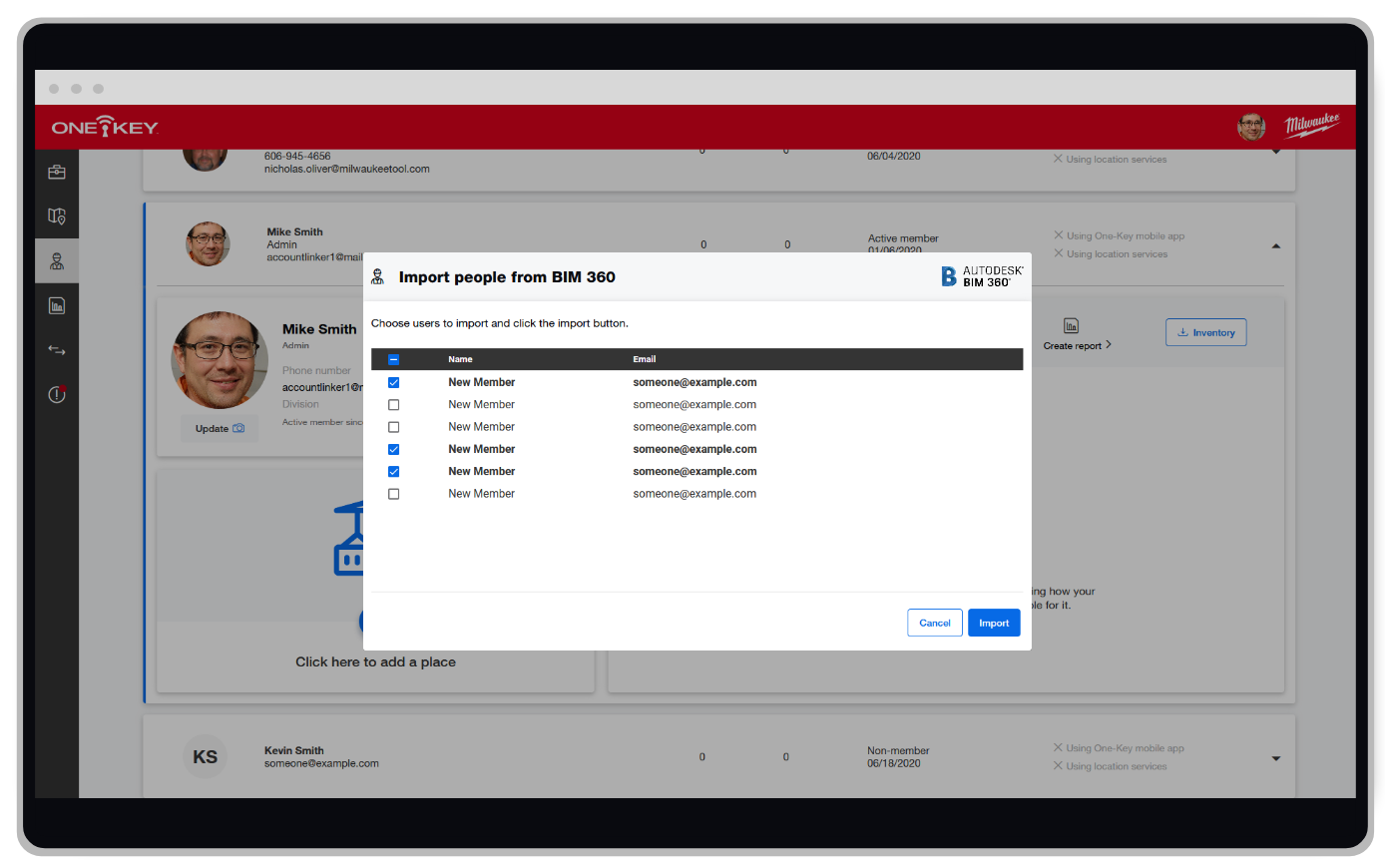 Costello agrees. “Understanding your data,” he explains, is one security principle that should be foundational for any company. “You need to understand the data that you have in your system, determine how you value that data, and then assign it a data classification so you are all speaking the same language internally.”
Costello agrees. “Understanding your data,” he explains, is one security principle that should be foundational for any company. “You need to understand the data that you have in your system, determine how you value that data, and then assign it a data classification so you are all speaking the same language internally.”
“You may value the subset of data you share with third party companies, or business partners, differently than they value the data,” he continues. “So, it's important for you as the customer to understand what data you're sharing and with whom you're sharing it. This will allow you to ensure the third party or business partner is placing a similar level of control around that data as you would put on it internally to your organization.”

“Let's say the data you are sharing is valued as confidential. You will want to ask your business partners, integration partners, etc., what general security controls they have in place and if there are any additional controls they place around this type of data. This will help ensure your data is protected in line with what you would expect.
Zach Costello, Sr. Product Security Manager·Milwaukee Tool
Costello explains this kind of data security is what the security industry refers to as third-party risk management. It’s critical, he expounds, and part of any admin’s responsibilities, “managing the third party to make sure they're going to handle your data in the appropriate way.”
To put this into context, integrating your One-Key account with the project team’s Procore account or the design team’s BIM 360 account can provide important data sharing between teams to eliminate duplicate project data and also help provide them speed to execute on building projects. However, it also potentially opens your company up to potential data leak concerns if proper controls aren’t put in place. It’s therefore important to ask questions like: “Who on these teams has access to what? Can we limit who has access to what (i.e., to only those on a need-to-know basis)?”
That’s where Costello’s next piece of advice about admins securing multi-user accounts comes into play:
Shore Up Multi-User Accounts and Ensure Proper Permissioning
Costello tells me that the multi-user admin feature within One-Key was engineered to give admins an extra layer of protection through permissioning at the account-level. 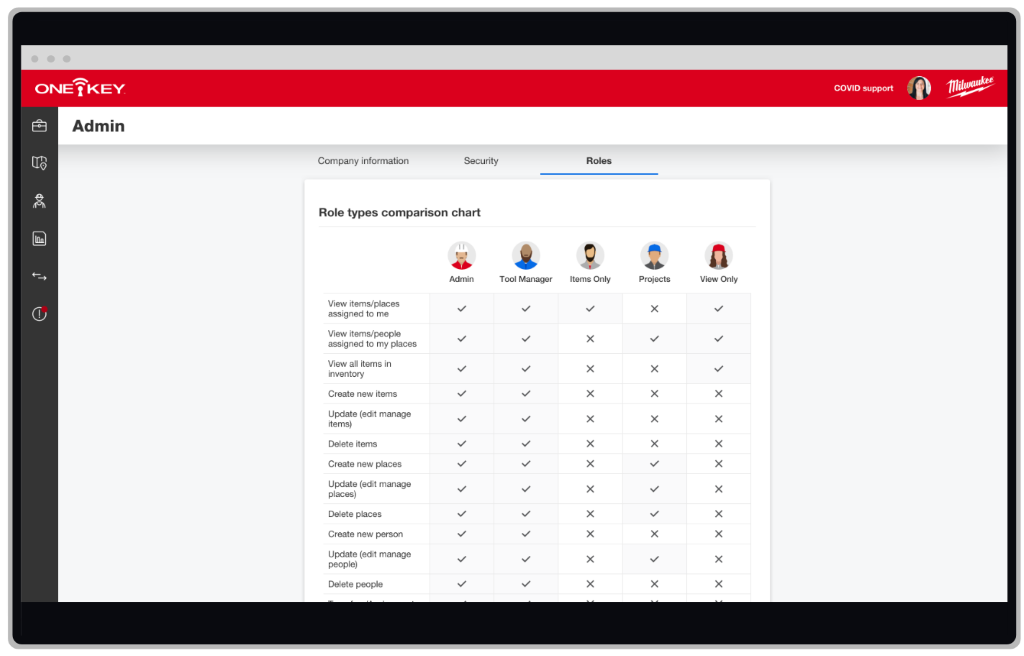 Prior to multi-user, the now-retired “guest” login introduced a certain degree of risk because it meant that any team member (whether a single, trusted ally or a whole team) looking to collaborate in a One-Key account had to share a guest password. A shared password, as you would imagine, is susceptible to leaking—whether through a data breach, a word-of-mouth exchange overheard by an unauthorized party, or the dreaded post-it note on the tool room’s computer monitor.
Prior to multi-user, the now-retired “guest” login introduced a certain degree of risk because it meant that any team member (whether a single, trusted ally or a whole team) looking to collaborate in a One-Key account had to share a guest password. A shared password, as you would imagine, is susceptible to leaking—whether through a data breach, a word-of-mouth exchange overheard by an unauthorized party, or the dreaded post-it note on the tool room’s computer monitor.
The new multi-user functionality shifts to individualized logins with specific, customizable roles that allow admins to ensure any new account creation is only given access to what the admin determines is necessary for that team member’s account (similar to your IT department dictating what a manager versus an employee has access to in Microsoft365).
Costello encourages admins to take advantage of the multi-user admin feature and role customization to shore up their One-Key account security: “If you are going to have multiple users in your account, I recommend highly using our multi-user feature that was implemented for a couple reasons – one of those being so that users don't share passwords. Password proliferation and reuse is an easy way for an attacker to compromise an account. Multi-user also allows you to set up roles for users in your account. This way, they have access to the right data at the right time, while limiting access to higher level admin functionality.”
The overall security of a One-Key account, Costello explains, is ultimately the responsibility of the admin. Therefore, he recommends a couple of tips:
- Customize role permissions – Limit the number of admins that are allowed on your account. You can provide as little access as “view-only” to tool managers able to transfer tools. That said, there should be a limited number of team members who have “God mode” as an admin, able to do everything (e.g., creating new accounts, deleting accounts, etc.) despite the convenience that may seem attractive to quickly grant those who might need access to more. The role customization feature allows you to edit a preset role and add/subtract what that role has access to – that way, you can create a capable role for the inventory manager you’ve hired to run your tool room while still paring it down, so they don’t have access to everything.
- Set up a process for outgoing employees – Costello says it’s good practice, in any part of the business, to “Have procedures in place so when users leave your team or organization you revoke access.” He recommends the same approach to multi-user One-Key accounts: “Make sure a procedure is in place so when someone leaves the team, the admin removes that user from the One-Key multi-user account.” He affords that, “It does then put a little bit more responsibility on the customer to manage the users in their account, but it is an important step to help safeguard their data from misuse.” Nonetheless, this little upfront effort to properly offboard an employee when they leave helps safeguard your account and prevent unauthorized use.
- Ensure employees practice good account-level security practice – A final consideration Costello offers, regardless of account permission level, is educating on proper cybersecurity practices for accounts. “It's pretty easy to reuse passwords and credentials from system to system, application to application. At some point that will get you into hot water. I highly recommend using a password manager as it is very difficult to remember a unique password for all the various systems most people interact with in a given day.” he explains. “You want to make sure the password you are using for One-Key is different than the password you're using for other sensitive accounts like email, social media, finances, business or anything like that.” He also recommends:
- “Make sure your passwords are unique application to application and of an appropriate length. So, something over 8 characters, but I would shoot for 12 to 16 depending on the type of data in that system. A password manager will help ensure the password is unique but also of sufficient length.”
- “Implementing some type of security program, and that's true of really anyone that is in a professional space. It doesn't have to be huge and should have some component of awareness, so employees know what security means to that organization.”
Ensure (and Educate Employees) Proper Settings Are Configured for Item-Level Tracking
Another consideration for inventory-related security is to ensure your tool team has proper education and (if applicable) is deploying the correct tracking hardware (and proper configuration of that hardware) to ensure the best performance for each application.
Barcoding may be useful around the tool room for checking in and out items or used in conjunction with a bulk send for quick auditing and reference.
That said, using One-Key compatible tools and trackers, Costello agrees, require proper understanding and education on how Bluetooth works and how settings need to be configured to get the best performance relative to what’s possible of Bluetooth tracking.
“From a One-Key perspective,” Costello explains, the app “does need location services for tracking and Bluetooth enabled to connect to the tool and change configuration settings. Bluetooth is also used to identify nearby tools. That data is then tied with the phone’s geolocation data and sent back to the application.”
Other ways we commonly recommend improving Bluetooth range:
- Encourage your employees have the app downloaded and Bluetooth and Location Services are enabled for the app. The more in the area using the app, the further the range.
- Have your app permissions set up so it’s running even when you don’t have the app open and aren’t actively using the app. This will ensure you’ll get the most up to date location updates, whether you’re in the app or not.
All this to say, education on GPS tracking (i.e., the One-Key tracking community does not use GPS technology) and where it might be used in place of Bluetooth is also important to ensure you’re applying the right capabilities for the precise scenario at hand.
Hire Cybersecurity Talent (and What to Look for)
Ultimately, managing cybersecurity as it relates to your asset inventory and One-Key account security is a shared responsibility between your admin and tool team. Proper education, application of account security best practices, and practicing cyber hygiene are an ongoing commitment to ensure your inventory data remains secure.  That said, hiring cybersecurity talent for your company is also an imperative as the industry becomes continually the target of ransomware campaigns.
That said, hiring cybersecurity talent for your company is also an imperative as the industry becomes continually the target of ransomware campaigns.
Costello offered some advice for what he, as a leader in the product security space, looks for when seeking both internal talent as well as what to look for from cybersecurity vendors:
- When looking for talent for an internal role, Costello says he looks for “Aptitude and a self-driven learning ability.” In a cybersecurity role, he explains “standing still” in one’s ability could mean “you’re falling behind.” “I’m looking for folks that are passionate about either the technology, security in general, or of their particular security domain.” He adds, “There’s a lot of different areas in the security space – compliance, incident response, engineering, architecture, all kinds of different hats you can wear. So, being passionate about that area and having an aptitude to develop further is key.
- When looking for vendors, he offers some of the following advice:
- “Look for well-known companies, that are respected in the industry. Gartner does a good job at identifying top vendors in the various security domains.”
- “Start small. The ultimate goal is to be better tomorrow than you are today. So, you can start small with a vendor or consultant and see how your relationship develops.”
- He admits that some security vendors have been known to take advantage of companies who may not know any better. To avoid being taken advantage of, he recommends to “Ask for references from similar companies, but most importantly ask for work samples. If you don’t like what you see, trust your gut, and move on.”
Bottom Line
The construction industry remains a hot target for cybercriminals likely due to its disjointed nature and many possible attack vectors that open throughout the process that attackers will look to exploit.
Furthermore, from a cybercriminal’s perspective, Costello explains, construction companies may be perceived as “easy to hold at ransom with the perception of having a lower security posture.”
All this to say, shoring up your security best practices and organizational education and training can help protect against potential hazards, keeping your first line of defense (your workers) empowered to keep attacks at bay.
Offering some parting thoughts, Costello remarked, “For anyone in the construction space, it’s important to understand that when you implement technology, it also comes with risk. You've got to look at the technology you're implementing, not only from the value it’s providing, but also what the added connectivity opens you up to from a risk perspective.”
Understanding the risk, he explains, is the first step in protecting against it.

Whitepaper
Digitize Your Inventory
In this white paper, learn 5 advantages of digitizing your construction inventory in the cloud. Increase productivity, limit downtime, & more.

About the Author
Lucas is Content Marketing and SEO Manager for Milwaukee Tool, where he and his team raise awareness about the company’s digital products and educate users on best practices through a variety of content vehicles. More Content By Lucas MarshallSubscribe to Our Blog
Sign up to receive ONE-KEY™ news and updates.
Recent Articles
Essential Strategies for Balancing Work and Life in Construction
Editorial Note: This article was brought to you courtesy of Rose Morrison, managing editor of ...
Maximizing Efficiency: Do Roofing and Scaffolding Specialists Need Construction Software?
Editorial Note: This article was brought to you courtesy of Rose Morrison, managing editor of ...
11 Advancements Women in Construction Have Made So Far This Year
Editorial Note: This article was brought to you courtesy of Rose Morrison, managing editor of ...



